In today's complex enterprise and commercial environment, Cybersecurity is more important than ever, and increasing in importance and complexity in an exponential rate.
In today’s complex enterprise and commercial environment, Cybersecurity is more important than ever, and increasing in importance and complexity in an exponential rate.
No matter the size of your business or the industry you operate in, especially in the past year, we have seen an exponential growth in remote employees. Whether you are a fully automated factory, a medical facility, a software company, a bank, a hospital or any other business your data is important and private. The biggest threat to you is your employees accessing your internal systems from their own homes, since they are usually the least protected networks and can endanger your entire system. Cylentium can provide you with our Zero Identity Network Cyber Security system, where we “bubble” all your employees networks and devices and your facilities creating a secure line of communication between all the connected and “bubbled” networks, where the data is end-to-end encrypted and invisible outside the protected “bubble”. Our technology is flexible and can travel with the users to any location providing the same level of protection and secure “bubble” with our wireless hotspot.
The Technology
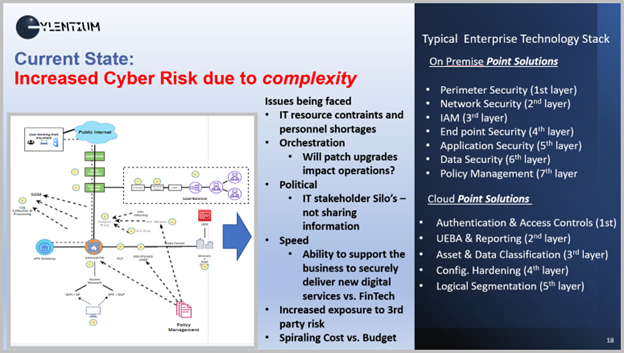
The diagram above represents the major challenges that all large enterprises – large to small SMB faces daily
The need to continually increase the amount of resourcing
The need to still have upgrades
Business can not wait for IT
Third Party Risk
Resiliency of the system
Cost keeps increasing
Security needs on Prem and in the Cloud
When will it stop?
Cylentium propose a new way of dealing with these challenges:
- We operate at Layer 2 (versus existing Layer 3 Technology)
- We render IP Addresses “INVISIBLE”. What they can’t see they can not detect
- We provide point to point Encryption (Symmetric and/or Asymmetric) throughout the enterprise, securing your data and ensuring compliance for regulators
- Full Asset Inventory Management. Allowing senior management to have confidence there are no unknown devices on the network knows
- All of the above wrapped in our “Policy Management Server”. Therefore, enabling RBAC and utilising ABAC to its full potential for Zero Trust Network Access Control
Cylentium is the only vendor qualified as a “Software-Defined Perimeter” utilising Microsegmentation
Cylentium is the only vendor offering Passwordless Technology based on Blockchain
