Government, Defense, & Intelligence
Cybersecurity in Government, Defense, & Intelligence is critical in these highly sensitive and hyper-shifting world.
Cylentium
Cylentium, Inc.’s cloaking software is currently protecting the Department of Energy’s (DOE) most sensitive nuclear reactor and storage sites. DOE recently approved the software for wider use as it was the only protection that withstood the 2019-20 “SolarWinds” cyber attack that penetrated DOE facilities across the US. This attack caused serious threats to national security and impacted nearly every industrial SCADA system targeted during the attack. The only networks not impacted were the ones with Cylentium software installed. The software also successfully protected our soldiers and civilians during the second Iraq War – guaranteeing mission assurance and safe operational movements. The software is offered to government agencies through GSD LLC, a wholly owned subsidiary of Cylentium, as the Advanced Crypto Enabled Unattributable Software Suite (ACEUSS).
Cylentium enables mission assurance by stopping attacks before they reach Layer 3 of your network, as it operates on perimeter masking network assets, as well as aids in finding the source of the attack, and allows for exploitation of an adversary without detection or attribution. ACEUSS operates at OSI Level 2; effectively cloaking to the point of complete invisibility the Internet Protocol (IP) address of any network, system, or device to which it is applied, while also protecting the operator’s operating identity/footprint and allowing for a distraction target to unwanted attackers. This method keeps unwanted/unauthorized intruders out of the network completely. Conventional software allows unauthorized intruders into networks with the decades old and costly Layer 3 protocol of Detect, Monitor, Mitigate. This strategy means the attacker is already in your network and detection could be hours to days before identified by current generation cyber protect protocols. ACEUSS represents next generation capabilities not available anywhere in the market today, enabling Zero Trust Architecture (ZTA) compliance for any network NOW.
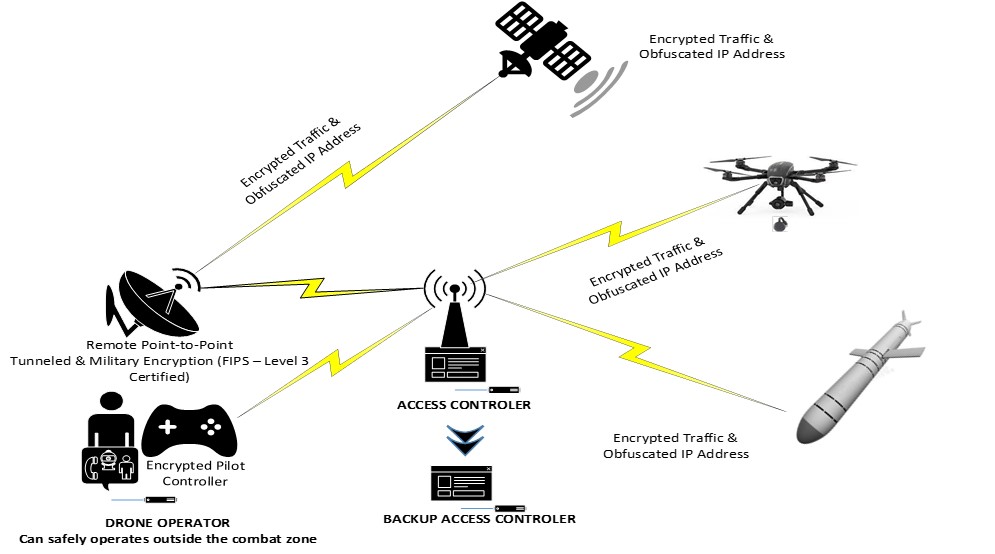
How It Works &
The Technology
The client software provides End-to-End uniform, strong security and enforces end point rules. This ensures that devices that are infected, unauthorized or do not meet policy standards are not allowed on the secure network.
(2) The second tier is comprised of one or more of Cylentium’s Access Controllers. Access Controllers enforce security policies, provide encryption, provide stream analysis, and enforce isolation of anomalous behavior or unauthorized devices.
Each Access Controller forms a load-balancing mesh network that provides resiliency and guarantees throughput. Failover and independent operations allow the Access Controllers to continue to operate in adverse conditions. Access Controllers are composed of microservices that allow:
(a) authentication and authorization of all devices
(b) encryption and decryption (if the frame is handled by this Access Controller)
(c) routing and mobility
(d) ARP and other low-level monitoring
(e) frame authentication, authenticity, and inspection
(f) enforcement of all policy rules
(g) stateful complex firewalling of traffic
(h) micro-segmentation of traffic
(i) management of anomalous behavior and unauthorized devices and
(j) forwards traffic to the policy server and other management systems for analysis through standard protocols.
(3) The third tier is comprised of one or more of Cylentium’s Policy Servers. A Policy Server is the command-and-control interface for the Cylentium System. Policy Servers:
(a) allow administrators to create and manage security policies
(b) integrate with Authentication and Authorization servers such as Active Directory (if desired)
(c) allows administrators to define the parameters that dictate behavior of the deployment (such as notification rules)
(d) allows an administrator to monitor and manage the system in real time
The combination of the features in our software allows the sensors to be authenticated and protected, allow end-to-end security for sensor devices, and keep the network monitored and safe.
