Technology
Cylentium is a Zero Identity Network Cyber Security system.
What we mean by that is that we at Cylentium, Inc. look at your cyber security
needs from a holistic point of view. Unlike most of the other cyber security
systems and technologies on the market, which are single device focused such as
Virtual Private Network (VPN) based systems, we are network focused, which
guarantees the same level of protection to all the devices connected to your
network.
What this means is that our security system cloaks your entire network
along with the devises connected to it from detection. If you are invisible to
cyber security threats, it is near impossible to target you for unauthorized
use or data leakage. Our goal is providing your network Zero Identity, so that
from the outside it looks like your network and your devices don’t even exist.
Because of our unique technology, we are a flexible,
full solution for your cyber security needs. We can provide the same level of protection
on any scale, no matter the number of people or devices you have on your
network. This is why our system works equally well in private homes, large
businesses or in military facilities. Whatever your needs are, we can
facilitate you. This is why we are a single solution cyber security provider.
The Technology
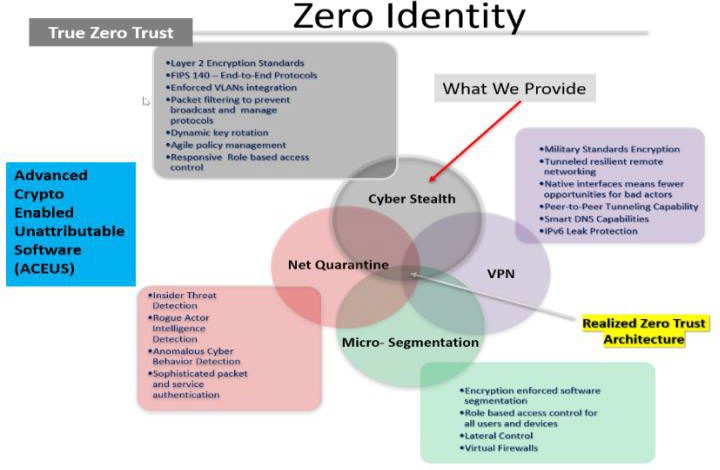
CYLENTIUM’s strategic mission and function are to protect the wireless and ethernet networks from visibility, detection and penetration.
Cylentium does this by enveloping the environments with cybersecurity “Bubbles”.
Cylentium hardens the environments in a “Non-Detectable”, “Non-Penetrable”, encrypted environment, protecting network traffic using FIPS 140-2 military approved algorithms and deeply sophisticated authentica-tion, in a software-only solution. Cylentium validates client conditions and states before allowing access and usage and monitors behaviour and patterns to ensure absolute cybersecurity compliance.
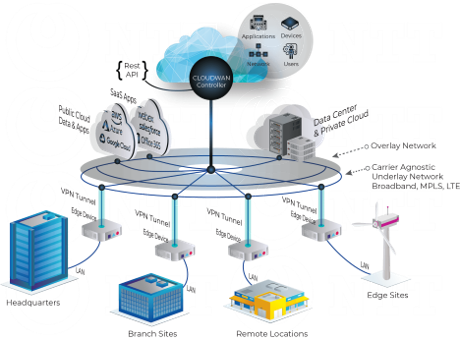
Cylentium can be embedded in organizations or manufactures existing equipment, routers, switches, bridges, and devices. Or, it can be deployed as a Cylentium certified standalone device. The Cylentium access devices can be dynamically deployed to ex-pand Bubble coverage to any imaginable size – from a cell phone to a city and beyond.
Cylentium Research is developing new AI and Machine Learning-based pattern detection that will also allow detection and pre-vention of data intrusion, data leakage, and malicious packet flow.
What is Cylentium?
Cylentium is a robust, Layer 2, FIPS 140—2 certified cybersecurity software solution that enables government agencies, healthcare organizations, enterprises, Industry, and your home and family, to enjoy the productivity benefits of wireless networks while minimizing security risks. Cylentium combines enterprise—class wireless network protection, seamless cross
—subnet mobility support, and integrated system management.
Due to the incredible flexibility of our technology, we are able to protect any type of networks. We achieve Zero Identity for your network by making it invisible, by encasing your network in a protected “bubble”. We have “bubbled” full military bases, naval fleets and even nuclear power plants. We can extend the protective “bubble” to fit your capacity. We provide the same level of protection on any scale and our pricing is based on your needs. This is why we can provide an affordable cyber security solution to consumers and institutional or enterprise clients alike.
What does it do?
Unlike virtual private network (VPN)—based systems, Cylentium’s Cylent encrypts full Ethernet frames, rather than just IP payloads, hiding vital information such as IP addresses, applications, and ports from unauthorized listeners. Frame-level encryption also protects non-data network traffic, including Dynamic Host Configuration Protocol (DHCP) requests or ARP messages, from being compromised and used to attack the network.
This approach helps protect both the user’s data and the organization’s network, while enabling users to securely roam across sub-nets without needing to re-authenticate or reboot their computers, saving time and minimizing frustration
Frequently Asked Questions
Would you like to submit a Question?
PPN (Personal Private Network) – Creates a secure and impenetrable shield around your WiFi (similar to a firewall, which protects a device, Cylentium protects your personal WiFi and all the devices connected to it (ie. smartphones, computers, smartTVs, smartwatches, home assistants (Alexa, Google Home), smart lights (Hue lights etc.), home security systems etc.)
How a regular VPN works: VPN secures the web traffic from your DEVICE to the server, your WiFi and all other devices connected to your WiFi are still vulnerable to monitoring and location tracking. VPN obscures your IP address (the physical location of your select device), not the web traffic (ie. your web traffic is still unprotected and visible, it just seems as if the action is coming from a different device/physical location)
How Cylentium PPN works: PPN secures all the web traffic from your WiFi and due to that all the devices connected to said WiFi to the server; PPN also includes VNP, but it is broader as PPN protects the internet access of your home/office, not just a single device you have VNP installed on
How Cylentium PPN works: PPN secures all the web traffic from your WiFi and due to that all the devices connected to said WiFi to the server; PPN also includes VNP, but it is broader as PPN protects the internet access of your home/office, not just a single device you have VNP installed on
– Broader protection
– Less likely for “human error” to cause security problems, as your IoT devices that have security issues (such as factory settings and passwords, weak passwords or in worst case no passwords that can compromise your entire network (such as smartlights))
– Let’s you control the access and permits of the devices on your WiFi
